authorizationPolicy详解
欢迎关注我的公众号:

目前刚开始写一个月,一共写了18篇原创文章,文章目录如下:
istio多集群探秘,部署了50次多集群后我得出的结论
istio多集群链路追踪,附实操视频
istio防故障利器,你知道几个,istio新手不要读,太难!
istio业务权限控制,原来可以这么玩
istio实现非侵入压缩,微服务之间如何实现压缩
不懂envoyfilter也敢说精通istio系列-http-rbac-不要只会用AuthorizationPolicy配置权限
不懂envoyfilter也敢说精通istio系列-02-http-corsFilter-不要只会vs
不懂envoyfilter也敢说精通istio系列-03-http-csrf filter-再也不用再代码里写csrf逻辑了
不懂envoyfilter也敢说精通istio系列http-jwt_authn-不要只会RequestAuthorization
不懂envoyfilter也敢说精通istio系列-05-fault-filter-故障注入不止是vs
不懂envoyfilter也敢说精通istio系列-06-http-match-配置路由不只是vs
不懂envoyfilter也敢说精通istio系列-07-负载均衡配置不止是dr
不懂envoyfilter也敢说精通istio系列-08-连接池和断路器
不懂envoyfilter也敢说精通istio系列-09-http-route filter
不懂envoyfilter也敢说精通istio系列-network filter-redis proxy
不懂envoyfilter也敢说精通istio系列-network filter-HttpConnectionManager
不懂envoyfilter也敢说精通istio系列-ratelimit-istio ratelimit完全手册
学习目标
#
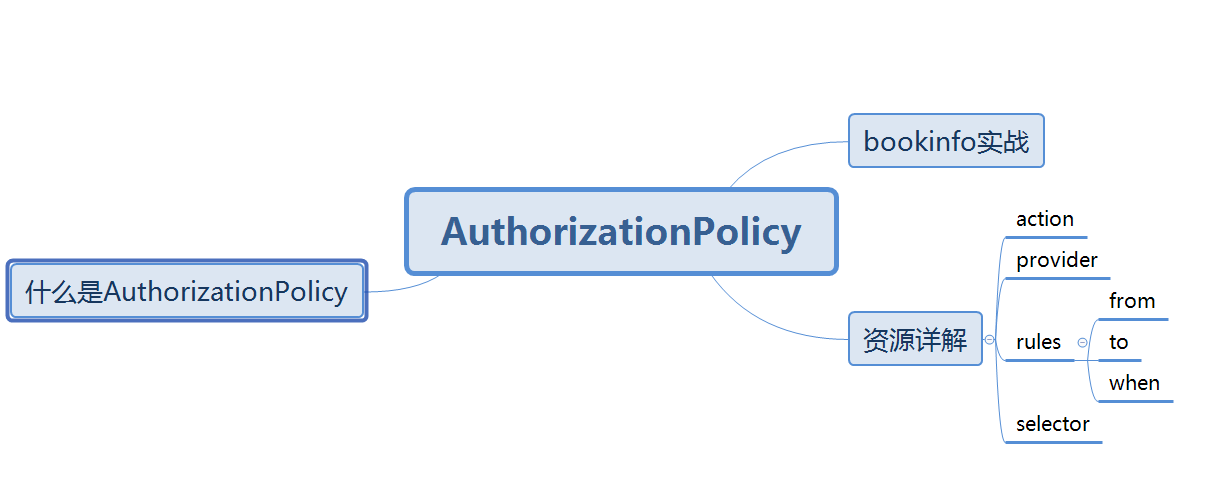
什么是AuthorizationPolicy
授权功能是 Istio 中安全体系的一个重要组成部分,它用来实现访问控制的功能,即判断一个请求是否允许通过,这个请求可以是从外部进入 Istio 内部的请求,也可以是在 Istio 内部从服务 A 到服务 B 的请求。可以把授权功能近似地认为是一种四层到七层的“防火墙”,它会像传统防火墙一样,对数据流进行分析和匹配,然后执行相应的动作。
流程
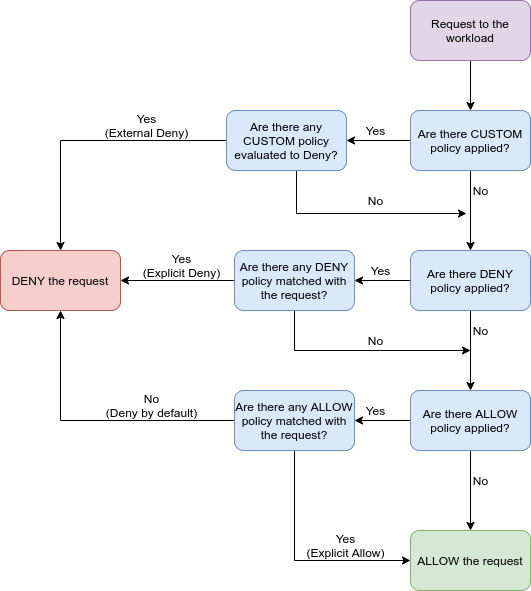
Authorization policies support ALLOW, DENY and CUSTOM actions. The policy precedence is CUSTOM, DENY and ALLOW. The following graph shows the policy precedence in detail:
资源详解
| Field | Type | Description | Required |
|---|---|---|---|
selector | WorkloadSelector | Optional. Workload selector decides where to apply the authorization policy. If not set, the authorization policy will be applied to all workloads in the same namespace as the authorization policy. | No |
rules | Rule[] | Optional. A list of rules to match the request. A match occurs when at least one rule matches the request.If not set, the match will never occur. This is equivalent to setting a default of deny for the target workloads. | No |
action | Action | Optional. The action to take if the request is matched with the rules. | No |
provider | ExtensionProvider (oneof) | Specifies detailed configuration of the CUSTOM action. Must be used only with CUSTOM action. | No |
允许nothing
allow-nothing.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: allow-nothingspec:# This matches nothing, the action defaults to ALLOW if not specified.{}
The following example shows an ALLOW policy that matches nothing. If there are no other ALLOW policies, requests will always be denied because of the “deny by default” behavior.
默认拒绝,有通过则通过
全局拒绝所有
kubectl apply -f global-deny-all.yaml -n istio-system
global-deny-all.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: deny-allnamespace: istio-systemspec:action: DENY# This matches everything.rules:- {}
名称空间拒绝所有
deny-all.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: deny-allspec:action: DENY# This matches everything.rules:- {}
名称空间级别
名称空间允许所有
allow-all.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: allow-allspec:action: ALLOWrules:- {}
名称空间级别
selector
productpage-allow-all.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpage-allow-allspec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- to:- operation:methods: ["GET", "POST"]
action
| Name | Description |
|---|---|
ALLOW | Allow a request only if it matches the rules. This is the default type. |
DENY | Deny a request if it matches any of the rules. |
AUDIT | Audit a request if it matches any of the rules. |
CUSTOM | The CUSTOM action allows an extension to handle the user request if the matching rules evaluate to true. The extension is evaluated independently and before the native ALLOW and DENY actions. When used together, A request is allowed if and only if all the actions return allow, in other words, the extension cannot bypass the authorization decision made by ALLOW and DENY action. Extension behavior is defined by the named providers declared in MeshConfig. The authorization policy refers to the extension by specifying the name of the provider. One example use case of the extension is to integrate with a custom external authorization system to delegate the authorization decision to it.Note: The CUSTOM action is currently an experimental feature and is subject to breaking changes in later versions. |
ALLOW
productpage-allow-all.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpage-allow-allspec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- to:- operation:methods: ["GET", "POST"]
DENY
1删除deny all
kubectl delete -f deny-all.yaml -n istio
2禁止访问produtpage
productpage-deny-allyaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpage-allow-allspec:selector:matchLabels:app: productpageversion: v1action: DENYrules:- {}
AUDIT
productpage-audit-all.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpage-allow-allspec:selector:matchLabels:app: productpageversion: v1action: AUDITrules:- {}
the only supported plugin is the Stackdriver plugin
需要安装audit插件
CUSTOM
The CUSTOM action is currently an experimental feature and is subject to breaking changes in later versions.
1创建opa策略
opa介绍
OPA-重新定义规则引擎-入门篇 | 菜鸟Miao
验证opa
The Rego Playground
policy.rego
package envoy.authzimport input.attributes.request.http as http_requestdefault allow = falsetoken = {"payload": payload} {[_, encoded] := split(http_request.headers.authorization, " ")[_, payload, _] := io.jwt.decode(encoded)}allow {action_allowed}bar := "bar"action_allowed {bar ==token.payload.foo}
2创建secret
kubectl create secret generic opa-policy —from-file policy.rego -n istio
3创建opa
opa-deployment.yaml
apiVersion: v1kind: Servicemetadata:name: opalabels:app: opaspec:ports:- name: grpcport: 9191targetPort: 9191selector:app: opa---kind: DeploymentapiVersion: apps/v1metadata:name: opalabels:app: opaspec:replicas: 1selector:matchLabels:app: opatemplate:metadata:labels:app: opaspec:containers:- name: opaimage: openpolicyagent/opa:latest-envoysecurityContext:runAsUser: 1111volumeMounts:- readOnly: truemountPath: /policyname: opa-policyargs:- "run"- "--server"- "--addr=localhost:8181"- "--diagnostic-addr=0.0.0.0:8282"- "--set=plugins.envoy_ext_authz_grpc.addr=:9191"- "--set=plugins.envoy_ext_authz_grpc.query=data.envoy.authz.allow"- "--set=decision_logs.console=true"- "--ignore=.*"- "/policy/policy.rego"ports:- containerPort: 9191livenessProbe:httpGet:path: /health?pluginsscheme: HTTPport: 8282initialDelaySeconds: 5periodSeconds: 5readinessProbe:httpGet:path: /health?pluginsscheme: HTTPport: 8282initialDelaySeconds: 5periodSeconds: 5volumes:- name: opa-policysecret:secretName: opa-policy
4编辑meshconfig
kubectl edit configmap istio -n istio-system
mesh: |-# Add the following contents:extensionProviders:- name: "opa.istio"envoyExtAuthzGrpc:service: "opa.istio.svc.cluster.local"port: "9191"
5闯将ap
ext-authz.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: ext-authznamespace: istio-systemspec:selector:matchLabels:app: istio-ingressgatewayaction: CUSTOMprovider:name: "opa.istio"rules:- to:- operation:paths: ["/productpage"]
6测试
TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjQ2ODU5ODk3MDAsImZvbyI6ImJhciIsImlhdCI6MTUzMjM4OTcwMCwiaXNzIjoidGVzdGluZ0BzZWN1cmUuaXN0aW8uaW8iLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.CfNnxWP2tcnR9q0vxyxweaF3ovQYHYZl82hAUsn21bwQd9zP7c-LS9qd_vpdLG4Tn1A15NxfCjp5f7QNBUo-KC9PJqYpgGbaXhaGx7bEdFWjcwv3nZzvc7M__ZpaCERdwU7igUmJqYGBYQ51vr2njU9ZimyKkfDe3axcyiBZde7G6dabliUosJvvKOPcKIWPccCgefSj_GNfwIip3-SsFdlR7BtbVUcqR-yv-XOxJ3Uc1MI0tz3uMiiZcyPV7sNCU4KRnemRIMHVOfuvHsU60_GhGbiSFzgPTAa9WTltbnarTbxudb_YEOx12JiwYToeX0DCPb43W1tzIBxgm8NxUg
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjM1MzczOTExMDQsImdyb3VwcyI6WyJncm91cDEiLCJncm91cDIiXSwiaWF0IjoxNTM3MzkxMTA0LCJpc3MiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyIsInNjb3BlIjpbInNjb3BlMSIsInNjb3BlMiJdLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.EdJnEZSH6X8hcyEii7c8H5lnhgjB5dwo07M5oheC8Xz8mOllyg—AHCFWHybM48reunF—oGaG6IXVngCEpVF0_P5DwsUoBgpPmK1JOaKN6_pe9sh0ZwTtdgK_RP01PuI7kUdbOTlkuUi2AO-qUyOm7Art2POzo36DLQlUXv8Ad7NBOqfQaKjE9ndaPWT7aexUsBHxmgiGbz1SyLH879f7uHYPbPKlpHU6P9S-DaKnGLaEchnoKnov7ajhrEhGXAQRukhDPKUHO9L30oPIr5IJllEQfHYtt6IZvlNUGeLUcif3wpry1R5tBXRicx2sXMQ7LyuDremDbcNy_iE76Upg
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
参考GitHub - istio-ecosystem/authservice: Move OIDC token acquisition out of your app code and into the Istio mesh
第三方授权服务
rules
| Field | Type | Description | Required |
|---|---|---|---|
from | From[] | Optional. from specifies the source of a request.If not set, any source is allowed. | No |
to | To[] | Optional. to specifies the operation of a request.If not set, any operation is allowed. | No |
when | Condition[] | Optional. when specifies a list of additional conditions of a request.If not set, any condition is allowed. | No |
from
| Field | Type | Description | Required |
|---|---|---|---|
source | Source | Source specifies the source of a request. | No |
| Field | Type | Description | Required |
|---|---|---|---|
principals | string[] | Optional. A list of source peer identities (i.e. service account), which matches to the “source.principal” attribute. This field requires mTLS enabled.If not set, any principal is allowed. | No |
notPrincipals | string[] | Optional. A list of negative match of source peer identities. | No |
requestPrincipals | string[] | Optional. A list of request identities (i.e. “iss/sub” claims), which matches to the “request.auth.principal” attribute.If not set, any request principal is allowed. | No |
notRequestPrincipals | string[] | Optional. A list of negative match of request identities. | No |
namespaces | string[] | Optional. A list of namespaces, which matches to the “source.namespace” attribute. This field requires mTLS enabled.If not set, any namespace is allowed. | No |
notNamespaces | string[] | Optional. A list of negative match of namespaces. | No |
ipBlocks | string[] | Optional. A list of IP blocks, which matches to the “source.ip” attribute. Populated from the source address of the IP packet. Single IP (e.g. “1.2.3.4”) and CIDR (e.g. “1.2.3.0/24”) are supported.If not set, any IP is allowed. | No |
notIpBlocks | string[] | Optional. A list of negative match of IP blocks. | No |
remoteIpBlocks | string[] | Optional. A list of IP blocks, which matches to the “remote.ip” attribute. Populated from X-Forwarded-For header or proxy protocol. To make use of this field, you must configure the numTrustedProxies field of the gatewayTopology under the meshConfig when you install Istio or using an annotation on the ingress gateway. See the documentation here: Configuring Gateway Network Topology. Single IP (e.g. “1.2.3.4”) and CIDR (e.g. “1.2.3.0/24”) are supported.If not set, any IP is allowed. | No |
notRemoteIpBlocks | string[] | Optional. A list of negative match of remote IP blocks. | No |
principals
productpage-rules-from-principals.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- from:- source:principals: ["cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account"]
notPrincipals
productpage-rules-from-notPrincipals.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- from:- source:notPrincipals: ["cluster.local/ns/istio-system/sa/test"]
requestPrincipals
The principal of the authenticated JWT token, constructed from the JWT claims in the format of /, requires request authentication policy applied
jwt相关
productpage-rules-from-requestPrincipals-star.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- to:- operation:notPaths: ["/healthz"]from:- source:requestPrincipals: ["*"]
1启用jwt
requestauthentications/ra-example-productpage.yaml
apiVersion: "security.istio.io/v1beta1"kind: "RequestAuthentication"metadata:name: "jwt-example"spec:selector:matchLabels:app: productpagejwtRules:- issuer: "testing@secure.istio.io"jwks: |{ "keys":[{"e":"AQAB","kid":"DHFbpoIUqrY8t2zpA2qXfCmr5VO5ZEr4RzHU_-envvQ","kty":"RSA","n":"xAE7eB6qugXyCAG3yhh7pkDkT65pHymX-P7KfIupjf59vsdo91bSP9C8H07pSAGQO1MV_xFj9VswgsCg4R6otmg5PV2He95lZdHtOcU5DXIg_pbhLdKXbi66GlVeK6ABZOUW3WYtnNHD-91gVuoeJT_DwtGGcp4ignkgXfkiEm4sw-4sfb4qdt5oLbyVpmW6x9cfa7vs2WTfURiCrBoUqgBo_-4WTiULmmHSGZHOjzwa8WtrtOQGsAFjIbno85jp6MnGGGZPYZbDAa_b3y5u-YpW7ypZrvD8BgtKVjgtQgZhLAGezMt0ua3DRrWnKqTZ0BJ_EyxOGuHJrLsn00fnMQ"}]}forwardOriginalToken: true
2使用authorizationPolicy
productpage-rules-from-requestPrincipals.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- to:- operation:paths: ["/productpage"]from:- source:requestPrincipals:- "testing@secure.istio.io/testing@secure.istio.io"
3访问
TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjQ2ODU5ODk3MDAsImZvbyI6ImJhciIsImlhdCI6MTUzMjM4OTcwMCwiaXNzIjoidGVzdGluZ0BzZWN1cmUuaXN0aW8uaW8iLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.CfNnxWP2tcnR9q0vxyxweaF3ovQYHYZl82hAUsn21bwQd9zP7c-LS9qd_vpdLG4Tn1A15NxfCjp5f7QNBUo-KC9PJqYpgGbaXhaGx7bEdFWjcwv3nZzvc7M__ZpaCERdwU7igUmJqYGBYQ51vr2njU9ZimyKkfDe3axcyiBZde7G6dabliUosJvvKOPcKIWPccCgefSj_GNfwIip3-SsFdlR7BtbVUcqR-yv-XOxJ3Uc1MI0tz3uMiiZcyPV7sNCU4KRnemRIMHVOfuvHsU60_GhGbiSFzgPTAa9WTltbnarTbxudb_YEOx12JiwYToeX0DCPb43W1tzIBxgm8NxUg
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjM1MzczOTExMDQsImdyb3VwcyI6WyJncm91cDEiLCJncm91cDIiXSwiaWF0IjoxNTM3MzkxMTA0LCJpc3MiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyIsInNjb3BlIjpbInNjb3BlMSIsInNjb3BlMiJdLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.EdJnEZSH6X8hcyEii7c8H5lnhgjB5dwo07M5oheC8Xz8mOllyg—AHCFWHybM48reunF—oGaG6IXVngCEpVF0_P5DwsUoBgpPmK1JOaKN6_pe9sh0ZwTtdgK_RP01PuI7kUdbOTlkuUi2AO-qUyOm7Art2POzo36DLQlUXv8Ad7NBOqfQaKjE9ndaPWT7aexUsBHxmgiGbz1SyLH879f7uHYPbPKlpHU6P9S-DaKnGLaEchnoKnov7ajhrEhGXAQRukhDPKUHO9L30oPIr5IJllEQfHYtt6IZvlNUGeLUcif3wpry1R5tBXRicx2sXMQ7LyuDremDbcNy_iE76Upg
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
验证token:
JSON Web Tokens - jwt.io
productpage-rules-from-requestPrincipals-semi-star.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- to:- operation:paths: ["/productpage"]from:- source:requestPrincipals:- "testing@secure.istio.io/*"
notRequestPrincipals
jwt相关
productpage-rules-from-notRequestPrincipals.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- to:- operation:paths: ["/productpage"]from:- source:notRequestPrincipals:- "testing@secure.istio.io/testing@secure.istio.io"
namespaces
productpage-rules-from-namespaces.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- from:- source:namespaces:- "istio-system"
notNamespaces
productpage-rules-from-notNamespaces.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- from:- source:notNamespaces:- "test"
ipBlocks
ingressgateway-rules-from-ipBlocks.yaml
kubectl apply -f ingressgateway-rules-from-ipBlocks.yaml -n istio-system
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: ingressgatewayspec:selector:matchLabels:app: istio-ingressgatewayaction: ALLOWrules:- from:- source:ipBlocks:- "172.20.0.0/16"
设置xff,原地址保持
notIpBlocks
ingressgateway-rules-from-notIpBlocks.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: ingressgatewayspec:selector:matchLabels:app: istio-ingressgatewayaction: ALLOWrules:- from:- source:notIpBlocks:- "172.20.0.0/16"
remoteIpBlocks
修改svc
kubectl edit svc istio-ingressgateway -n istio-system
externalTrafficPolicy: Local
用于设置白名单
ingressgateway-rules-from-remoteIpBlocks.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: ingressgatewayspec:selector:matchLabels:app: istio-ingressgatewayaction: DENYrules:- from:- source:remoteIpBlocks:- 192.168.198.1/32
notRemoteIpBlocks
修改svc
kubectl edit svc istio-ingressgateway -n istio-system
externalTrafficPolicy: Local
用于设置黑名单
ingressgateway-rules-from-notRemoteIpBlocks.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: ingressgatewayspec:selector:matchLabels:app: istio-ingressgatewayaction: ALLOWrules:- from:- source:notRemoteIpBlocks:- "192.168.198.1/32
to
| Field | Type | Description | Required |
|---|---|---|---|
operation | Operation | Operation specifies the operation of a request. | No |
| Field | Type | Description | Required |
|---|---|---|---|
hosts | string[] | Optional. A list of hosts, which matches to the “request.host” attribute.If not set, any host is allowed. Must be used only with HTTP. | No |
notHosts | string[] | Optional. A list of negative match of hosts. | No |
ports | string[] | Optional. A list of ports, which matches to the “destination.port” attribute.If not set, any port is allowed. | No |
notPorts | string[] | Optional. A list of negative match of ports. | No |
methods | string[] | Optional. A list of methods, which matches to the “request.method” attribute. For gRPC service, this will always be “POST”.If not set, any method is allowed. Must be used only with HTTP. | No |
notMethods | string[] | Optional. A list of negative match of methods. | No |
paths | string[] | Optional. A list of paths, which matches to the “request.url_path” attribute. For gRPC service, this will be the fully-qualified name in the form of “/package.service/method”.If not set, any path is allowed. Must be used only with HTTP. | No |
notPaths | string[] | Optional. A list of negative match of paths. | No |
hosts
productpage-rules-to-hosts.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- to:- operation:hosts:- "bookinfo.demo:30986"from:- source:namespaces:- "istio-system"
details-rules-to-hosts.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:hosts:- "details:9080"
其实是authority,必须加上端口
notHosts
productpage-rules-to-notHosts.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- to:- operation:notHosts:- "test"from:- source:namespaces:- "istio-system"
ports
details-rules-to-ports.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:ports:- "9080"
notPorts
details-rules-to-notPorts.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:notPorts:- "9080"
methods
details-rules-to-methods.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:methods:- "GET"
notMethods
details-rules-to-notMethods.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:notMethods:- "GET"
paths
details-rules-to-paths.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:paths:- "/details/0"
统配符
details-rules-to-paths-star.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:paths:- "/details/*"
notPaths
details-rules-to-notPaths.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:notPaths:- "/details/0"
通配符
details-rules-to-notPaths-star.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: detailsspec:selector:matchLabels:app: detailsversion: v1action: ALLOWrules:- to:- operation:notPaths:- "/details/*"
when
| Field | Type | Description | Required |
|---|---|---|---|
key | string | The name of an Istio attribute. See the full list of supported attributes. | Yes |
values | string[] | Optional. A list of allowed values for the attribute. Note: at least one of values or not_values must be set. | No |
notValues | string[] | Optional. A list of negative match of values for the attribute. Note: at least one of values or not_values must be set. | No |
https://istio.io/latest/docs/reference/config/security/conditions/
| Name | Description | Supported Protocols | Example |
|---|---|---|---|
request.headers | HTTP request headers. The header name is surrounded by [] without any quotes | HTTP only | key: request.headers[User-Agent] values: [“Mozilla/“] |
source.ip | Source workload instance IP address, supports single IP or CIDR | HTTP and TCP | key: source.ip values: [“10.1.2.3”, “10.2.0.0/16”] |
remote.ip | Original client IP address as determined by X-Forwarded-For header or Proxy Protocol, supports single IP or CIDR | HTTP and TCP | key: remote.ip values: [“10.1.2.3”, “10.2.0.0/16”] |
source.namespace | Source workload instance namespace, requires mutual TLS enabled | HTTP and TCP | key: source.namespace values: [“default”] |
source.principal | The identity of the source workload, requires mutual TLS enabled | HTTP and TCP | key: source.principal values: [“cluster.local/ns/default/sa/productpage”] |
request.auth.principal | The principal of the authenticated JWT token, constructed from the JWT claims in the format of /, requires request authentication policy applied | HTTP only | key: request.auth.principal values: [“issuer.example.com/subject-admin”] |
request.auth.audiences | The intended audiences of the authenticated JWT token, constructed from the JWT claim | ||
request.auth.presenter | The authorized presenter of the authenticated JWT token, constructed from the JWT claim | ||
request.auth.claims | Raw claims of the authenticated JWT token. The claim name is surrounded by [] without any quotes, nested claim can also be used, requires request authentication policy applied. Note only support claim of type string or list of string | HTTP only | key: request.auth.claims[iss] values: [“@foo.com”] — key: request.auth.claims[nested1][nested2] values: [“some-value”] |
destination.ip | Destination workload instance IP address, supports single IP or CIDR | HTTP and TCP | key: destination.ip values: [“10.1.2.3”, “10.2.0.0/16”] |
destination.port | Destination workload instance port, must be in the range [0, 65535]. Note this is not the service port | HTTP and TCP | key: destination.port values: [“80”, “443”] |
connection.sni | The server name indication, requires TLS enabled | HTTP and TCP | key: connection.sni values: [“www.example.com”] |
experimental.envoy.filters.* | Experimental metadata matching for filters, values wrapped in [] are matched as a list | HTTP and TCP | key: experimental.envoy.filters.network.mysql_proxy[db.table] values: [“[update]”] |
| field | sub field | JWT claims |
|---|---|---|
| from.source | requestPrincipals | iss/sub |
| from.source | notRequestPrincipals | iss/sub |
| when.key | request.auth.principal | iss/sub |
| when.key | request.auth.audiences | aud |
| when.key | request.auth.presenter | azp |
| when.key | request.auth.claims[key] | JWT 全部属性 |
request.headers
values
productpage-rules-when-request-headers-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.headers[test]values:- "test"
curl 192.168.198.154:30986/productpage —header “test:test”
notValues
productpage-rules-when-request-headers-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.headers[test]notValues:- "test"
curl 192.168.198.154:30986/productpage —header “test:test”
curl 192.168.198.154:30986/productpage —header “test:test2”
source.ip
values
productpage-when-source-ip-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- when:- key: source.ipvalues:- "172.20.0.0/16"
notValues
productpage-when-source-ip-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- when:- key: source.ipnotValues:- "172.20.0.0/16"
remote.ip
修改svc
kubectl edit svc istio-ingressgateway -n istio-system
externalTrafficPolicy: Local
黑白名单
values
productpage-when-remote-ip-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: DENYrules:- when:- key: remote.ipvalues:- "192.168.198.1/32"
notValues
productpage-when-remote-ip-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- when:- key: remote.ipnotValues:- "192.168.198.1/32"
source.namespace
values
productpage-when-source-namespace-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- when:- key: source.namespacevalues:- "istio-system"
notValues
productpage-when-source-namespace-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageaction: ALLOWrules:- when:- key: source.namespacenotValues:- "istio-system"
source.principal
values
productpage-when-source-principal-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: source.principalvalues:- "cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account"
notValues
productpage-when-source-principal-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: source.principalnotValues:- "cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account"
request.auth.principal
jwt相关
values
productpage-when-request-auth-principal-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.principalvalues:- "testing@secure.istio.io/testing@secure.istio.io"
TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjM1MzczOTExMDQsImdyb3VwcyI6WyJncm91cDEiLCJncm91cDIiXSwiaWF0IjoxNTM3MzkxMTA0LCJpc3MiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyIsInNjb3BlIjpbInNjb3BlMSIsInNjb3BlMiJdLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.EdJnEZSH6X8hcyEii7c8H5lnhgjB5dwo07M5oheC8Xz8mOllyg—AHCFWHybM48reunF—oGaG6IXVngCEpVF0_P5DwsUoBgpPmK1JOaKN6_pe9sh0ZwTtdgK_RP01PuI7kUdbOTlkuUi2AO-qUyOm7Art2POzo36DLQlUXv8Ad7NBOqfQaKjE9ndaPWT7aexUsBHxmgiGbz1SyLH879f7uHYPbPKlpHU6P9S-DaKnGLaEchnoKnov7ajhrEhGXAQRukhDPKUHO9L30oPIr5IJllEQfHYtt6IZvlNUGeLUcif3wpry1R5tBXRicx2sXMQ7LyuDremDbcNy_iE76Upg
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
notValues
productpage-when-request-auth-principal-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.principalnotValues:- "testing@secure.istio.io/testing@secure.istio.io"
TOKEN=eyJhbGciOiJSUzI1NiIsImtpZCI6IkRIRmJwb0lVcXJZOHQyenBBMnFYZkNtcjVWTzVaRXI0UnpIVV8tZW52dlEiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjM1MzczOTExMDQsImdyb3VwcyI6WyJncm91cDEiLCJncm91cDIiXSwiaWF0IjoxNTM3MzkxMTA0LCJpc3MiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyIsInNjb3BlIjpbInNjb3BlMSIsInNjb3BlMiJdLCJzdWIiOiJ0ZXN0aW5nQHNlY3VyZS5pc3Rpby5pbyJ9.EdJnEZSH6X8hcyEii7c8H5lnhgjB5dwo07M5oheC8Xz8mOllyg—AHCFWHybM48reunF—oGaG6IXVngCEpVF0_P5DwsUoBgpPmK1JOaKN6_pe9sh0ZwTtdgK_RP01PuI7kUdbOTlkuUi2AO-qUyOm7Art2POzo36DLQlUXv8Ad7NBOqfQaKjE9ndaPWT7aexUsBHxmgiGbz1SyLH879f7uHYPbPKlpHU6P9S-DaKnGLaEchnoKnov7ajhrEhGXAQRukhDPKUHO9L30oPIr5IJllEQfHYtt6IZvlNUGeLUcif3wpry1R5tBXRicx2sXMQ7LyuDremDbcNy_iE76Upg
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
request.auth.audiences
相当于request.auth.claims[aud]
values
productpage-when-request-auth-audiences-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.audiencesvalues:- "app"- “web”
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
notValues
productpage-when-request-auth-audiences-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.audiencesnotValues:- "app"- “web”
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
request.auth.presenter
相当于request.auth.claims[azp]
authorized presenter
values
productpage-when-request-auth-presenter-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.presentervalues:- "app"
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
notValues
productpage-when-request-auth-presenter-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.presenternotValues:- "app"
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
request.auth.claims
jwt相关
values
productpage-when-request-auth-claims-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.claims[groups]values:- "group1"
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
notValues
productpage-when-request-auth-claims-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: request.auth.claims[groups]notValues:- "group1"
curl 192.168.198.154:30986/productpage -H “Authorization: Bearer ${TOKEN}“
destination.ip
values
productpage-when-destination-ip-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: destination.ipvalues:- "172.20.0.0/16"
notValues
productpage-when-destination-ip-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: destination.ipnotValues:- "172.20.0.0/16"
destination.port
values
productpage-when-destination-port-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: destination.portvalues:- "9080"
notValues
productpage-when-destination-port-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: destination.portnotValues:- "9080"
connection.sni
values
productpage-when-connection-sni-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: connection.snivalues:- "outbound_.9080_._.productpage.istio.svc.cluster.local"
requestedServerName的值
notValues
productpage-when-connection-sni-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: connection.sninotValues:- "outbound_.9080_._.productpage.istio.svc.cluster.local"
experimental.envoy.filters.*
试验性的
暂时不验证
values
productpage-when-envoy-filters-mysql_proxy-values.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: experimental.envoy.filters.network.mysql_proxy[db.table]values:- "[update]"
notValues
productpage-when-envoy-filters-mysql_proxy-notValues.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:selector:matchLabels:app: productpageversion: v1action: ALLOWrules:- when:- key: experimental.envoy.filters.network.mysql_proxy[db.table]notValues:- "[update]"
组合配置
productpage-complex.yaml
apiVersion: security.istio.io/v1beta1kind: AuthorizationPolicymetadata:name: productpagespec:action: ALLOWrules:- from:- source:principals:- cluster.local/ns/istio-system/sa/istio-ingressgateway-service-accountnamespaces:- istio-systemto:- operation:methods: ["GET"]paths: ["/productpage"]- operation:methods: ["GET"]paths: ["/static/*"]- operation:methods: ["GET"]paths: ["/api/v1/products/*"]- operation:methods: ["GET"]paths: ["/logout"]- operation:methods: ["POST"]paths: ["/login"]when:- key: source.ipvalues:- "172.20.0.0/16"
Dependency on mutual TLS
Istio uses mutual TLS to securely pass some information from the client to the server. Mutual TLS must be enabled before using any of the following fields in the authorization policy:
- the
principalsandnotPrincipalsfield under thesourcesection - the
namespacesandnotNamespacesfield under thesourcesection - the
source.principalcustom condition - the
source.namespacecustom condition
Mutual TLS is not required if you don’t use any of the above fields in the authorization policy.



































还没有评论,来说两句吧...